What is StoreManager Update.exe?
StoreManager Update.exe is part of SetupBuilder and developed by Lindersoft according to the StoreManager Update.exe version information.
StoreManager Update.exe's description is "SetupBuilder "
StoreManager Update.exe is digitally signed by OptiLeaf, Inc..
StoreManager Update.exe is usually located in the 'c:\downloads\' folder.
Some of the anti-virus scanners at VirusTotal detected StoreManager Update.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Vendor and version information [?]
The following is the available information on StoreManager Update.exe:
| Property | Value |
|---|---|
| Product name | SetupBuilder |
| Company name | Lindersoft |
| File description | SetupBuilder |
| Legal copyright | Copyright (C) Linder Software |
| Product version | 10, 0, 0, 4 |
| File version | 10, 0, 0, 4 |
Here's a screenshot of the file properties when displayed by Windows Explorer:
| Product name | SetupBuilder .. |
| Company name | Lindersoft .. |
| File description | SetupBuilder .. |
| Legal copyright | Copyright (C) Linder Software .. |
| Product version | 10, 0, 0, 4 |
| File version | 10, 0, 0, 4 |
Digital signatures [?]
StoreManager Update.exe has a valid digital signature.
| Property | Value |
|---|---|
| Signer name | OptiLeaf, Inc. |
| Certificate issuer name | COMODO RSA Code Signing CA |
| Certificate serial number | 00dc458216fc4df44fdc150bcec944cde0 |
VirusTotal report
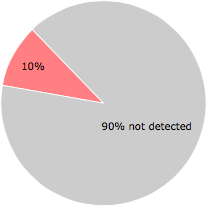
7 of the 67 anti-virus programs at VirusTotal detected the StoreManager Update.exe file. That's a 10% detection rate.
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5750.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5740.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5752.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"file_recreated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp"
],
"directory_created": [
"C:\\Users\\cuck\\AppData",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck",
"C:\\Users",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\1dbddc40-21e7-11ea-4823-01dd8d3c0029"
],
"dll_loaded": [
"UXTHEME",
"SETUPAPI.dll",
"RICHED32.DLL",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"kernel32.dll",
"UxTheme.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"rpcrt4.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Windows\\system32\\uxtheme.dll",
"ole32.dll",
"user32.dll",
"comctl32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5750.tmp",
"C:\\Users",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5740.tmp",
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Users\\cuck\\Documents\\desktop.ini",
"C:\\Users\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5752.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\Favorites\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"regkey_opened": [
"HKEY_CLASSES_ROOT\\Drive\\shellex\\FolderExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Setup",
"HKEY_CURRENT_USER\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{DAC9ABC0-295A-11E8-5F90-0C8D15516952}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLEAUT",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OLE\\Tracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{DAC9ABC0-295A-11E8-5F90-0C8D15516952}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_CLASSES_ROOT\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5750.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5740.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5752.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5750.tmp",
"",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5740.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5752.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"directory_removed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\1dbddc40-21e7-11ea-4823-01dd8d3c0029"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\wupdate.ini",
"C:\\Users\\cuck\\Desktop",
"C:\\Users\\cuck\\AppData\\Local\\Temp"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\1dbddc40-21e7-11ea-4823-01dd8d3c0029"
],
"command_line": [
"explorer.exe"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\Documents\\desktop.ini",
"C:\\Users\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"C:\\Users\\cuck\\Favorites\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\RegisteredOwner",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorUseSystemHeap",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\ProgramFilesDir",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\CommonFilesDir",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}\\DriveMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorSystemHeapIsPrivate",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\RegisteredOrganization"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\1dbddc40-21e7-11ea-4823-01dd8d3c0029\\*.*"
]
}Dropped
[
{
"yara": [],
"sha1": "74ae6d5d995552c7197a87ca2a43daae8521fed7",
"name": "1e326faf6548fffa_~SB5740.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5740.tmp",
"type": "PC bitmap, Windows 3.x format, 164 x 314 x 8",
"sha256": "1e326faf6548fffa8682948f7cbf96d93766526fa0733ce0b0075140b36fc201",
"urls": [],
"crc32": "6F3D76DF",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/1e326faf6548fffa_~SB5740.tmp",
"ssdeep": null,
"size": 52574,
"sha512": "83ecada9c7ca90294fb2edbb1e7e3f890e7fd578412a7281dd3ed1a973be126871a1d7b2ff3886097152a9db66019a9bd3ffbba799200f5bdb594752717d1a00",
"pids": [
2740
],
"md5": "757342f504ab9aa2c1216d75247835ff"
},
{
"yara": [
{
"meta": {
"description": "Possibly employs anti-virtualization techniques",
"author": "nex"
},
"name": "vmdetect",
"offsets": {
"virtualpc": [
[
210797,
0
]
]
},
"strings": [
"Dz8HCw=="
]
}
],
"sha1": "a609adb693c8267183135b502307fec9bbdad377",
"name": "e216dfb131d72754_LSB572E.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"type": "PE32 executable (DLL) (GUI) Intel 80386, for MS Windows",
"sha256": "e216dfb131d72754804ae1a808c835593a2412008a00df2225cd2f0b2f538867",
"urls": [],
"crc32": "6A3E2579",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/e216dfb131d72754_LSB572E.tmp",
"ssdeep": null,
"size": 311808,
"sha512": "e9009a47a115cc354c5da7de81492f93e77b450cfe5a2aa5db3d9f09dad9421890c6c5db27e5e5ab308e8dbf3408410e5383244c5e1f807f7bc741c3c951016a",
"pids": [
2740
],
"md5": "70d109f091320f6713f8a1348ea209d6"
},
{
"yara": [],
"sha1": "d520058483923dfefe39ebb10d2cd33e5232da90",
"name": "354483eea7318ec5_354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"type": "PE32 executable (GUI) Intel 80386, for MS Windows",
"sha256": "354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242",
"urls": [
"http:\/\/ocsp.comodoca.com0",
"https:\/\/secure.comodo.net\/CPS0C",
"https:\/\/www.globalsign.com\/repository\/0",
"http:\/\/crl.comodoca.com\/COMODORSACertificationAuthority.crl0q",
"http:\/\/crl.comodoca.com\/COMODORSACodeSigningCA.crl0t",
"http:\/\/secure.globalsign.com\/cacert\/gstimestampingsha2g2.crt0",
"http:\/\/crl.globalsign.com\/gs\/gstimestampingsha2g2.crl0",
"http:\/\/crt.comodoca.com\/COMODORSACodeSigningCA.crt0",
"https:\/\/www.globalsign.com\/repository\/06",
"http:\/\/ocsp2.globalsign.com\/gstimestampingsha2g20",
"http:\/\/crl.globalsign.net\/root-r3.crl0",
"http:\/\/crt.comodoca.com\/COMODORSAAddTrustCA.crt0"
],
"crc32": "3B04ECCA",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/354483eea7318ec5_354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"ssdeep": null,
"size": 220336,
"sha512": "d1751af6ef364d05704f1e2ab892cb61c57294fdc03ac0e9c83bad53e6e65db960bad94ccb77a269ba86094ee05697c1831c1309690684d2159d59f6d28710fa",
"pids": [],
"md5": "800e348a7b4206d2d0aa5bc0e1f9a12e"
},
{
"yara": [],
"sha1": "e80ab06d88bc687b18d2d71860751a9866f2464d",
"name": "aa47d189bc0d7c80_~SB5752.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5752.tmp",
"type": "ASCII text, with CRLF line terminators",
"sha256": "aa47d189bc0d7c8090b69f21370cbdd4b057da822190cb102c94e5590b6714a7",
"urls": [],
"crc32": "FF208F19",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/aa47d189bc0d7c80_~SB5752.tmp",
"ssdeep": null,
"size": 854,
"sha512": "4f1b57bb02be077a8826af0c72ba8cbad1c5121f7e1aedd99e3c87e3fa64e9e7654fbb25941178f7200f8ebdbd601e97fe8018026bef0ecb78bb2a360c66286f",
"pids": [
2740
],
"md5": "34ca396200f61b3dadf72aae9bb6db8a"
},
{
"yara": [],
"sha1": "0ed778ef9ca412aaa0f3ccb6416f5071a4ec8ce8",
"name": "a797253b53bde211_~SB5B7E.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"type": "PE32 executable (GUI) Intel 80386, for MS Windows",
"sha256": "a797253b53bde211d11c9648df364423ef4b7810d95b57a9bf877bfc754efbae",
"urls": [
"http:\/\/ocsp.comodoca.com0",
"https:\/\/secure.comodo.net\/CPS0C",
"https:\/\/www.globalsign.com\/repository\/0",
"http:\/\/crl.comodoca.com\/COMODORSACertificationAuthority.crl0q",
"http:\/\/crl.comodoca.com\/COMODORSACodeSigningCA.crl0t",
"http:\/\/secure.globalsign.com\/cacert\/gstimestampingsha2g2.crt0",
"http:\/\/crl.globalsign.com\/gs\/gstimestampingsha2g2.crl0",
"http:\/\/crt.comodoca.com\/COMODORSACodeSigningCA.crt0",
"https:\/\/www.globalsign.com\/repository\/06",
"http:\/\/ocsp2.globalsign.com\/gstimestampingsha2g20",
"http:\/\/crl.globalsign.net\/root-r3.crl0",
"http:\/\/crt.comodoca.com\/COMODORSAAddTrustCA.crt0"
],
"crc32": "4B78418E",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/a797253b53bde211_~SB5B7E.tmp",
"ssdeep": null,
"size": 212288,
"sha512": "7e27cd56ed0aa35d440d4d20fc3c923179beadd9ea4f5eb044351cfdf23d3a31045d95daab4dfc6669cd50c125252979fe3b90082cb9814d425b63c5693a70f8",
"pids": [
2740
],
"md5": "66bbec839b901c56f59266b10df10f65"
},
{
"yara": [],
"sha1": "0408da8473bc9c3045c431f8458aed2792928cc3",
"name": "b770b92ae5dccc57_~SB5764.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"type": "ASCII text, with CRLF line terminators",
"sha256": "b770b92ae5dccc57c98d14ebf1c7f3c907bd7e44801676b172664eb91ce36869",
"urls": [],
"crc32": "03E91D42",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/b770b92ae5dccc57_~SB5764.tmp",
"ssdeep": null,
"size": 400,
"sha512": "228c2b6dc32afab0b75ea5cf031ae96230f2962a4720a8675db5f3fd1a23bffb42390c764c4671b0cc89c6835a977c0068c64f46b1786428523b0c593008578b",
"pids": [
2740
],
"md5": "f4ec98f5628db72a0cd05bcdbad46a5f"
},
{
"yara": [],
"sha1": "c4e450743d64e31772b800b65c1e64fedd3c88e9",
"name": "422170900f338182_LSB571D.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"type": "PE32 executable (DLL) (GUI) Intel 80386, for MS Windows",
"sha256": "422170900f338182eaac2a321a3314493ac819d61749ae24c30eda887cdb912b",
"urls": [],
"crc32": "A6D67B93",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/422170900f338182_LSB571D.tmp",
"ssdeep": null,
"size": 15360,
"sha512": "83d647ec334fc48175a0cc7419fb99a5db02068ddd1960080c870f2d1a92957d1a0ee9314e85a8f5b7731d33b465d97a7c72ca83390eeabbbeb83e2cbd7a5ee7",
"pids": [
2740
],
"md5": "e69d2c26200b14e0270f1a0c62b8712a"
},
{
"yara": [
{
"meta": {
"description": "Matched shellcode byte patterns",
"author": "nex"
},
"name": "shellcode",
"offsets": {
"shell6": [
[
2025,
0
]
]
},
"strings": [
"VYvsgew="
]
}
],
"sha1": "798aa81c52b89117924a05d9443a428af7312a0c",
"name": "3fe16539247ed8de_LSB571C.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"type": "MS Compress archive data",
"sha256": "3fe16539247ed8de1659b64db9a4f04e889acd3d9e2f9e121c15d8578cdbbc92",
"urls": [],
"crc32": "E3EF2BAC",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/3fe16539247ed8de_LSB571C.tmp",
"ssdeep": null,
"size": 9387,
"sha512": "51a699bbba46eae63a96d5d1cf4a60aed7a253951b1a4303fc1dabdbb926eff83daec3cda8a3f04b90f05b2984495c7bc99d93f6d4b92f3172cd50d95a9740d7",
"pids": [
2740
],
"md5": "7d39a0d57c42b21f96a52cef022ec17a"
},
{
"yara": [],
"sha1": "91e0c824899a84198e07182879b4121d73de3564",
"name": "36ff279812aa58c7_~SB5750.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5750.tmp",
"type": "PC bitmap, Windows 3.x format, 55 x 55 x 8",
"sha256": "36ff279812aa58c73187e9e858da474275e03bb0c94c12d3ec09be54d1b8b212",
"urls": [],
"crc32": "A37DB3BB",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/36ff279812aa58c7_~SB5750.tmp",
"ssdeep": null,
"size": 4158,
"sha512": "ddee20259eb0d237310a078a8e0bdabe3d1dc944e11b352a670b54a8c8cdd1e9ea7ba03e47e2826df27558baf3867484cf54469def360bec5e0b73eadec9cd4a",
"pids": [
2740
],
"md5": "776025e09cf2ee3f5220ffac192b779a"
},
{
"yara": [],
"sha1": "7d10b6bb08cad65226712612a15eb0bc525d455b",
"name": "859e9cd0feebb008_~SB5766.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"type": "data",
"sha256": "859e9cd0feebb0082cfd66bdc56fee88536fe91b8a0452f67357d0ce4d89d6c4",
"urls": [],
"crc32": "541F70A6",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/859e9cd0feebb008_~SB5766.tmp",
"ssdeep": null,
"size": 17382,
"sha512": "a8e60712a5befe2c4779f4e53c272b2ea96e38a6a726bae64532f1ac159ff507aa03dee42e6bfd765cbfd75f75c1cc5a2bc555ac156267a22db8acbc7dd2f676",
"pids": [
2740
],
"md5": "58b2755cf98445388f40e7871c76755e"
},
{
"yara": [],
"sha1": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
"name": "e3b0c44298fc1c14_LSB572E.tmp",
"type": "empty",
"sha256": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
"urls": [],
"crc32": "00000000",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/e3b0c44298fc1c14_LSB572E.tmp",
"ssdeep": null,
"size": 0,
"sha512": "cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce47d0d13c5d85f2b0ff8318d2877eec2f63b931bd47417a81a538327af927da3e",
"md5": "d41d8cd98f00b204e9800998ecf8427e"
},
{
"yara": [],
"sha1": "5570711d8ec84d233a2b03fe5497343cdaf4bf68",
"name": "09e3f4fe84e3f831_~SB5751.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"type": "PE32 executable (DLL) (GUI) Intel 80386, for MS Windows",
"sha256": "09e3f4fe84e3f8317842eed7c19b8185417ee6522213ed07b780c2f85189bcd9",
"urls": [],
"crc32": "F9A4545A",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/09e3f4fe84e3f831_~SB5751.tmp",
"ssdeep": null,
"size": 9728,
"sha512": "20731cd107055694857cbcb1b9df51a2f2d613f8afc200f1f70e6010395ed65639fa7db16739e0b0bd2470802a674e64e7d9d782037e5b675e43ebca2639cc9a",
"pids": [
2740
],
"md5": "4650ae9be4ad7db580f120431a49bf73"
},
{
"yara": [],
"sha1": "86caa8c696aeee3e83cefd0c50a0ae4f200bd64c",
"name": "4039d396126c460f_~SB5763.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp",
"type": "data",
"sha256": "4039d396126c460fe5c0dfa11d9b1339114457d1a9aa2cb9a7a8984104823042",
"urls": [
"http:\/\/ocsp.comodoca.com0",
"https:\/\/secure.comodo.net\/CPS0C",
"https:\/\/www.globalsign.com\/repository\/0",
"http:\/\/crl.comodoca.com\/COMODORSACertificationAuthority.crl0q",
"http:\/\/crl.comodoca.com\/COMODORSACodeSigningCA.crl0t",
"http:\/\/secure.globalsign.com\/cacert\/gstimestampingsha2g2.crt0",
"http:\/\/crl.globalsign.com\/gs\/gstimestampingsha2g2.crl0",
"http:\/\/crt.comodoca.com\/COMODORSACodeSigningCA.crt0",
"https:\/\/www.globalsign.com\/repository\/06",
"http:\/\/ocsp2.globalsign.com\/gstimestampingsha2g20",
"http:\/\/crl.globalsign.net\/root-r3.crl0",
"http:\/\/crt.comodoca.com\/COMODORSAAddTrustCA.crt0"
],
"crc32": "3E820D04",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/4039d396126c460f_~SB5763.tmp",
"ssdeep": null,
"size": 6581,
"sha512": "1735b09e5cd3b347d70e91d9669ae9b75b2f5aa3bb8158d0f8ec061f7eec45c8235bb21886deead9d832710e494e8c2e3a258cd6745c32018136335827447776",
"pids": [
2740
],
"md5": "749666ee9026ae9fa72c3b2d26d5ba70"
},
{
"yara": [],
"sha1": "15f9c370689417f7f412f08a11aa694c287c9570",
"name": "f2d3ebae272b8ccb_~SB5765.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"type": "ASCII text, with CRLF line terminators",
"sha256": "f2d3ebae272b8ccb422a6e76f5ac81ef340ed2c802ede06f3fc45242dd3ce90b",
"urls": [],
"crc32": "DBFF5701",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/f2d3ebae272b8ccb_~SB5765.tmp",
"ssdeep": null,
"size": 16126,
"sha512": "42ce8bcb29938d7c2ca6b4c934c5595afc8e4ff9da34cf4d32173bb60464f3609465265430e956343e2ff0db3450b74e6ec5d9f81a640ba9fa29ecf4db2b276e",
"pids": [
2740
],
"md5": "1afd17f9ba88ea13cf18babadf88a230"
},
{
"yara": [],
"sha1": "c10a362c7ad35976348e4215e7f36a8edd5638a3",
"name": "2998c0302672f877_~SB573F.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"type": "ASCII text, with CRLF line terminators",
"sha256": "2998c0302672f877e5963fde10603291350fc6231f3deee606cb15f0f74a132c",
"urls": [],
"crc32": "64FA2535",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4365\/files\/2998c0302672f877_~SB573F.tmp",
"ssdeep": null,
"size": 13207,
"sha512": "d6aae1cdebb1e87fc2246613061a0b62afda54bdacfcc082078488b72ed2ed32bf8c074d18e2f3eeba18fa9decefb73050b1f46fcdcb29d0bebb6537631207d6",
"pids": [
2740
],
"md5": "f219eb1753049d05ba415dde4f6a733c"
}
]Generic
[
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1576687985.34375,
"ppid": 376
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"process_name": "354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"pid": 2740,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5750.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5740.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5752.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"file_recreated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp"
],
"directory_created": [
"C:\\Users\\cuck\\AppData",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck",
"C:\\Users",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\1dbddc40-21e7-11ea-4823-01dd8d3c0029"
],
"dll_loaded": [
"UXTHEME",
"SETUPAPI.dll",
"RICHED32.DLL",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"kernel32.dll",
"UxTheme.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"rpcrt4.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Windows\\system32\\uxtheme.dll",
"ole32.dll",
"user32.dll",
"comctl32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5750.tmp",
"C:\\Users",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5740.tmp",
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Users\\cuck\\Documents\\desktop.ini",
"C:\\Users\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5752.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\Favorites\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"regkey_opened": [
"HKEY_CLASSES_ROOT\\Drive\\shellex\\FolderExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Setup",
"HKEY_CURRENT_USER\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{DAC9ABC0-295A-11E8-5F90-0C8D15516952}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLEAUT",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OLE\\Tracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{DAC9ABC0-295A-11E8-5F90-0C8D15516952}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_CLASSES_ROOT\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5750.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5740.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5752.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5750.tmp",
"",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5740.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5752.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"directory_removed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\1dbddc40-21e7-11ea-4823-01dd8d3c0029"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\wupdate.ini",
"C:\\Users\\cuck\\Desktop",
"C:\\Users\\cuck\\AppData\\Local\\Temp"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\1dbddc40-21e7-11ea-4823-01dd8d3c0029"
],
"command_line": [
"explorer.exe"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5766.tmp",
"C:\\Users\\cuck\\Documents\\desktop.ini",
"C:\\Users\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5765.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB573F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"C:\\Users\\cuck\\Favorites\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5764.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571C.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5763.tmp"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\RegisteredOwner",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorUseSystemHeap",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\ProgramFilesDir",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\RegisteredOrganization",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\CommonFilesDir",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}\\DriveMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorSystemHeapIsPrivate",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\1dbddc40-21e7-11ea-4823-01dd8d3c0029\\*.*"
]
},
"first_seen": 1576687985.65625,
"ppid": 1664
},
{
"process_path": "C:\\Windows\\SysWOW64\\explorer.exe",
"process_name": "explorer.exe",
"pid": 964,
"summary": {
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
]
},
"first_seen": 1576687990.577625,
"ppid": 2740
}
]Signatures
[
{
"markcount": 1,
"families": [],
"description": "Checks if process is being debugged by a debugger",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741811,
"api": "IsDebuggerPresent",
"return_value": 0,
"arguments": {},
"time": 1576687986.82825,
"tid": 2588,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 2876
}
],
"references": [],
"name": "checks_debugger"
},
{
"markcount": 1,
"families": [],
"description": "Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "GlobalMemoryStatusEx",
"return_value": 1,
"arguments": {},
"time": 1576687986.92225,
"tid": 1676,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3489
}
],
"references": [],
"name": "antivm_memory_available"
},
{
"markcount": 12,
"families": [],
"description": "One or more processes crashed",
"severity": 1,
"marks": [
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "L\nS\nU\nn\np\na\nc\nk\n+\n0\nx\n2\n8\n7\n \nl\ns\nb\n5\n7\n1\nd\n+\n0\nx\n2\n6\n1\n7\n \n@\n \n0\nx\n1\n0\n0\n0\n2\n6\n1\n7\n\n\n3\n5\n4\n4\n8\n3\ne\ne\na\n7\n3\n1\n8\ne\nc\n5\na\nf\n3\nb\n8\n5\nd\nf\n0\nf\nd\n5\n3\n5\n0\n1\n2\n6\nc\nf\n5\n5\n9\n3\n8\n8\nc\n3\n4\n1\nb\nf\n0\nc\n4\n2\na\n3\n1\nf\na\n8\nb\nd\n9\n2\n4\n2\n+\n0\nx\n1\na\n0\n2\n \n@\n \n0\nx\n9\nf\n1\na\n0\n2",
"registers": {
"esp": 2752024,
"edi": 0,
"eax": 10429521,
"ebp": 2752072,
"edx": 2130565971,
"ebx": 0,
"esi": 269057408,
"ecx": 269057408
},
"exception": {
"instruction_r": "88 10 40 89 45 e4 41 89 4d e0 ff 4d 10 eb e6 39",
"symbol": "lstrcpyn+0x2d lstrlen-0x53 kernelbase+0xa2dd",
"instruction": "mov byte ptr [eax], dl",
"module": "KERNELBASE.dll",
"exception_code": "0xc0000005",
"offset": 41693,
"address": "0x75dba2dd"
}
},
"time": 1576687985.78125,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 79
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nc\n9\nd\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n0\n8\nc\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n0\n8\nc\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\n2\ne\n8\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\n6\nd\n7\n \n@\n \n0\nx\n1\n0\n0\n2\n1\n6\nd\n7\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\nd\n7\nc\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n0\n1\n6\nb\n \n@\n \n0\nx\n1\n0\n0\n2\n0\n1\n6\nb",
"registers": {
"esp": 2784432,
"edi": 1975271054,
"eax": 2784256,
"ebp": 2784472,
"edx": 0,
"ebx": 268694932,
"esi": 268684080,
"ecx": 5117784
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.84425,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 2931
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nb\n5\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\nf\n4\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n1\nf\n4\n8\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n4\nd\n7\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n4\n1\n6\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n4\n1\n6\n8",
"registers": {
"esp": 2679096,
"edi": 1975271054,
"eax": 2679088,
"ebp": 2679136,
"edx": 0,
"ebx": 268687036,
"esi": 268687036,
"ecx": 5117864
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.90625,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3437
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nb\n5\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\nf\n4\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n1\nf\n4\n8\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n5\ne\na\ne\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n5\n2\n9\nd\n \n@\n \n0\nx\n1\n0\n0\n2\n5\n2\n9\nd",
"registers": {
"esp": 2679108,
"edi": 1975271054,
"eax": 2679040,
"ebp": 2679148,
"edx": 0,
"ebx": 270265408,
"esi": 270265408,
"ecx": 5117800
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.90625,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3442
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nc\n9\nd\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n0\n8\nc\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n0\n8\nc\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n5\ne\na\ne\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n5\n2\n9\nd\n \n@\n \n0\nx\n1\n0\n0\n2\n5\n2\n9\nd",
"registers": {
"esp": 2679108,
"edi": 1975271054,
"eax": 2679040,
"ebp": 2679148,
"edx": 0,
"ebx": 268694932,
"esi": 268684080,
"ecx": 5117784
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.90625,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3443
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nb\n5\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\nf\n4\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n1\nf\n4\n8\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n5\ne\na\ne\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n5\n2\n9\nd\n \n@\n \n0\nx\n1\n0\n0\n2\n5\n2\n9\nd",
"registers": {
"esp": 2679108,
"edi": 1975271054,
"eax": 2679040,
"ebp": 2679148,
"edx": 0,
"ebx": 270265408,
"esi": 270265408,
"ecx": 5117848
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.92225,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3444
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nb\n5\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\nf\n4\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n1\nf\n4\n8\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n5\ne\na\ne\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n5\n2\n9\nd\n \n@\n \n0\nx\n1\n0\n0\n2\n5\n2\n9\nd",
"registers": {
"esp": 2679108,
"edi": 1975271054,
"eax": 2679107,
"ebp": 2679148,
"edx": 0,
"ebx": 270265408,
"esi": 270265408,
"ecx": 5117408
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.92225,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3445
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nb\n5\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\nf\n4\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n1\nf\n4\n8\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\nf\na\ne\n5\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\ne\ne\nd\n4\n \n@\n \n0\nx\n1\n0\n0\n2\ne\ne\nd\n4",
"registers": {
"esp": 2679108,
"edi": 1975271054,
"eax": 2679040,
"ebp": 2679148,
"edx": 0,
"ebx": 268686864,
"esi": 268686864,
"ecx": 5114144
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.92225,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3448
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nb\n5\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\nf\n4\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n1\nf\n4\n8\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\nf\na\nf\n1\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\ne\ne\ne\n0\n \n@\n \n0\nx\n1\n0\n0\n2\ne\ne\ne\n0",
"registers": {
"esp": 2679096,
"edi": 1975271054,
"eax": 2679040,
"ebp": 2679136,
"edx": 0,
"ebx": 268694900,
"esi": 268694900,
"ecx": 5114160
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.92225,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3449
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nb\n5\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\nf\n4\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n1\nf\n4\n8\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\nf\na\nf\nd\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\ne\ne\ne\nc\n \n@\n \n0\nx\n1\n0\n0\n2\ne\ne\ne\nc",
"registers": {
"esp": 2679084,
"edi": 1975271054,
"eax": 2679040,
"ebp": 2679124,
"edx": 0,
"ebx": 268694920,
"esi": 268694920,
"ecx": 5114192
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.92225,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3450
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nb\n5\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\nf\n4\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n1\nf\n4\n8\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\nf\nb\n0\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\ne\ne\nf\n8\n \n@\n \n0\nx\n1\n0\n0\n2\ne\ne\nf\n8",
"registers": {
"esp": 2679072,
"edi": 1975271054,
"eax": 2679040,
"ebp": 2679112,
"edx": 0,
"ebx": 268684508,
"esi": 268684508,
"ecx": 5114208
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687986.92225,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3451
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nd\nb\n7\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n2\n1\na\n6\n \n@\n \n0\nx\n1\n0\n0\n2\n2\n1\na\n6\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n2\nb\n5\n9\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n1\nf\n4\n8\n \n@\n \n0\nx\n1\n0\n0\n2\n1\nf\n4\n8\n\n\nR\nu\nn\nI\nn\ns\nt\na\nl\nl\ne\nr\n+\n0\nx\n6\n1\n3\n4\n \nl\ns\nb\n5\n7\n2\ne\n+\n0\nx\n2\n5\n5\n2\n3\n \n@\n \n0\nx\n1\n0\n0\n2\n5\n5\n2\n3",
"registers": {
"esp": 2679096,
"edi": 1975271054,
"eax": 2679040,
"ebp": 2679136,
"edx": 0,
"ebx": 268686864,
"esi": 268686864,
"ecx": 5114144
},
"exception": {
"instruction_r": "88 02 41 42 84 c0 75 f6 c7 45 fc fe ff ff ff 8b",
"symbol": "lstrcpy+0x18 GetWindowsDirectoryA-0x55 kernel32+0x32ab5",
"instruction": "mov byte ptr [edx], al",
"module": "kernel32.dll",
"exception_code": "0xc0000005",
"offset": 207541,
"address": "0x75be2ab5"
}
},
"time": 1576687988.62525,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3534
}
],
"references": [],
"name": "raises_exception"
},
{
"markcount": 5,
"families": [],
"description": "Drops an executable to the user AppData folder",
"severity": 2,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB572E.tmp",
"type": "ioc",
"description": null
},
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin",
"type": "ioc",
"description": null
},
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5B7E.tmp",
"type": "ioc",
"description": null
},
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\LSB571D.tmp",
"type": "ioc",
"description": null
},
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\~SB5751.tmp",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "exe_appdata"
},
{
"markcount": 2,
"families": [],
"description": "Queries for potentially installed applications",
"severity": 2,
"marks": [
{
"call": {
"category": "registry",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741772,
"api": "RegOpenKeyExA",
"return_value": 2,
"arguments": {
"access": "0x00000201",
"base_handle": "0x80000002",
"key_handle": "0x00000000",
"regkey": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{DAC9ABC0-295A-11E8-5F90-0C8D15516952}",
"regkey_r": "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{DAC9ABC0-295A-11E8-5F90-0C8D15516952}",
"options": 0
},
"time": 1576687986.92225,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3446
},
{
"call": {
"category": "registry",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741772,
"api": "RegOpenKeyExA",
"return_value": 2,
"arguments": {
"access": "0x00000201",
"base_handle": "0x80000001",
"key_handle": "0x00000000",
"regkey": "HKEY_CURRENT_USER\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{DAC9ABC0-295A-11E8-5F90-0C8D15516952}",
"regkey_r": "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{DAC9ABC0-295A-11E8-5F90-0C8D15516952}",
"options": 0
},
"time": 1576687986.92225,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 3447
}
],
"references": [],
"name": "queries_programs"
},
{
"markcount": 1,
"families": [],
"description": "Allocates execute permission to another process indicative of possible code injection",
"severity": 3,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 964,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0x0000007c",
"base_address": "0x0014f000"
},
"time": 1576687988.79725,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 3571
}
],
"references": [],
"name": "allocates_execute_remote_process"
},
{
"markcount": 1,
"families": [],
"description": "Deletes executed files from disk",
"severity": 3,
"marks": [
{
"category": "file",
"ioc": "",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "deletes_executed_files"
},
{
"markcount": 1,
"families": [],
"description": "Potential code injection by writing to the memory of another process",
"severity": 3,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 964,
"buffer": "\u0080\u00f0\u0014\u0000SV\u008bt$\fWj\u00ff\u008d\u00be\u0004\u0002\u0000\u0000\u00ff73\u00db\u00ff\u0096\b\u0002\u0000\u0000\u00ff7\u00ff\u0096\f\u0002\u0000\u0000\u008d\u00be(\u0002\u0000\u0000\u00eb\u0011C\u0083\u00fb\u0003\u0016h\u00e8\u0003\u0000\u0000\u00ff\u0096\u0014\u0002\u0000\u0000W\u00ff\u0096\u0010\u0002\u0000\u0000\u0085\u00c0t\u00e4\u0083\u00be$\u0002\u0000\u0000\u0001um\u008d\u0086,\u0003\u0000\u0000P\u00ff\u0096\u001c\u0002\u0000\u0000\u008d\u00be0\u0004\u0000\u0000W\u00ff\u0096 \u0002\u0000\u0000\u0085\u00c0t\u0007W\u00ff\u0096\u001c\u0002\u0000\u0000\u008d\u00be4\u0005\u0000\u0000W\u00ff\u0096 \u0002\u0000\u0000\u0085\u00c0t\u0007W\u00ff\u0096\u001c\u0002\u0000\u0000\u008d\u00be8\u0006\u0000\u0000W\u00ff\u0096 \u0002\u0000\u0000\u0085\u00c0t\u0007W\u00ff\u0096\u001c\u0002\u0000\u0000\u008d\u00be<\u0007\u0000\u0000W\u00ff\u0096 \u0002\u0000\u0000\u0085\u00c0t\u0007W\u00ff\u0096\u001c\u0002\u0000\u0000j\u0000\u00ff\u0096\u0018\u0002\u0000\u0000_^[\u00c3U\u008d\u00ac$\u0004\u00f2\u00ff\u00ff\u0081\u00ec|\u000e\u0000\u0000\u00a1\f1\u009f\u00003\u00c5\u0089\u0085\u00f8\r\u0000\u0000SVWj@3\u00f6\u008dE\u0084VP\u00c7E\u0080D\u0000\u0000\u0000\u00e8U\u00fe\u00ff\u00ffh\u0003\u0001\u0000\u0000\u008d\u0085\u00f1\u000b\u0000\u0000VP\u00c6\u0085\u00f0\u000b\u0000\u0000\u0000\u00e8<\u00fe\u00ff\u00ff\u008b=\u0010 \u009f\u0000\u0083\u00c4\u0018\u00bb\u0004!\u009f\u0000S\u008d\u0085\u00f0\u000b\u0000\u0000P\u0089u\u00d8\u00ff\u00d7\u008b5\\ \u009f\u0000h\u0000!\u009f\u0000\u008d\u0085\u00f0\u000b\u0000\u0000P\u00ff\u00d6h\u00fc \u009f\u0000\u008d\u0085\u00f0\u000b\u0000\u0000P\u00ff\u00d6h\u00f8 \u009f\u0000\u008d\u0085\u00f0\u000b\u0000\u0000P\u00ff\u00d6h\u00f4 \u009f\u0000\u008d\u0085\u00f0\u000b\u0000\u0000P\u00ff\u00d6h\u00f0 \u009f\u0000\u008d\u0085\u00f0\u000b\u0000\u0000P\u00ff\u00d6S\u008d\u0085\u00f0\u000b\u0000\u0000P\u00ff\u00d6h\u00ec \u009f\u0000\u008d\u0085\u00f0\u000b\u0000\u0000P\u00ff\u00d6S\u008d\u0085\u00f0\u000b\u0000\u0000P\u00ff\u00d6\u008dE\u00c8P\u008dE\u0080Ph\u00e8 \u009f\u00003\u00c0PjDPPP\u008d\u008d\u00f0\u000b\u0000\u0000QP\u00ff\u0015X \u009f\u0000\u0085\u00c0\u000f\u0084\\\u0002\u0000\u0000\u00a1T \u009f\u0000\u0089\u0085\u00b4\u0004\u0000\u0000\u00a1P \u009f\u0000\u008b\u001dL \u009f\u0000\u008b5\u0014 \u009f\u0000\u0089\u0085\u00bc\u0004\u0000\u0000\u00a1H \u009f\u0000\u0089\u0085\u00c0\u0004\u0000\u0000\u00a1D \u009f\u0000\u0089\u0085\u00c4\u0004\u0000\u0000\u00a1\u0004\u0000\u0000\u00006\u0011\u00bcu\u0010\u0014\u00bcuDT\u00bcu\u00ff\u0010\u00bcu\u0010z\u00bcu\u00bfD\u00c4uKZ\u00bcu\u0000\u0000\u0000\u0000C:\\Users\\cuck\\AppData\\Local\\Temp\\354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin\u0000\u0000\u0000\u0000\u0080(\u0000\u00f8\u00ff*\u0000\u0000\u0000\u0000\u0000\u000b\u0000\u0000\u0000X\u00ae\u00dcc\u00a5\u001a\u00dcc\u0091\u0015\u00decK\u0099\u00dcu\u0014\u0084\u00ddcH\u009c\u00dcu\u0004\u00a5\u00bcu\u00d8\u009f\u00dccm\u00ddcB\u0090\u00dcu\u0010\u001b\u009f\u00005\t\u00dec \u0097\u00dcu\u0014\u0084\u00ddcH\u009c\u00dcu\u0004\u00a5\u00bcu\u00d8\u009f\u00dccm\u00ddcB\u0090\u00dcu\u0010\u001b\u009f\u0000\u0000\u0000\u0000\u0000p\u00f6*\u0000\u00c8u\u00dcc\u00ff\u00ff\u00ff\u00ff\u0000\u0000J\u0000\u0000\u0010\u0000\u0000\u0000\u0080\u0000\u0000\u0090\u00f7*\u0000\u0001\u0005\u00e2c\u00a0\u00f6*\u0000\u00e7\u00cb\u00dcc\u0000\u0000J\u0000\u0000\u0010\u0000\u0000\u0000\u0080\u0000\u0000\rz\u00dccC:\\Users\\cuck\\AppData\\Local\\Temp\u0000\u000054483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242.bin\u0000\u0000\u0000B\u0000\u0000\u00008z_\u0000\u0018\u00f7*\u00004\u0000\u0000\u0000\u0018\u0000\u0000\u0000\u0000\u0000\u0000\u0000P\u00e8_\u0000(w_\u0000Tx_\u0000\u00f0a`\u0000(}_\u0000\u00f6\u0015\u00dec\u00b4\u00f6*\u0000\u0000\u0000\u0000\u0000\u00d4\u00fd*\u0000\u00cd\u001e\u00c0w\u00f2\u00a4\u001d\u0000\u00fe\u00ff\u00ff\u00ffl\u00e3\u00bbw\u00d2\u00e0\u00bbw\u0000\u0000\u0000\u0000x\u00fb*\u0000\u0000\u0000\u0000\u0000\fb`\u0000\u00e8\u00beb\u0000\fb`\u0000\u0000\u0000\u0000\u0000\u00e8\u00beb\u0000\u00a0\u00f7*\u0000\u0085H\u00bcw\u00d8 \u00c9w\u0000\u0000\u0000\u0000\u00f0a`\u0000\u0000\u0000\u0000\u0000X\u00ae\u00dcc\u0000\u0000\u0000\u0000\u0000\u0000_\u0000XYara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 546,
"time": 3.138896942138672,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 5226,
"time": 9.125553131103516,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7070,
"time": 3.0168960094451904,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7398,
"time": 1.0464510917663574,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7726,
"time": 3.0242130756378174,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8054,
"time": 1.5518031120300293,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8382,
"time": -0.09607505798339844,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 8710,
"time": 1.5631990432739258,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 24978,
"time": 1.0799229145050049,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 33362,
"time": 3.1450281143188477,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "595f8f804c03746b71ca6d0fd123d517864905bd0af67f6e02800e168b8e90d6",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "57b22c52f331cdff55cff6c776cfb994a5e234a74e6709bc7b31225eed4551fc",
"irc": [],
"https_ex": []
}Screenshots
StoreManager Update.exe removal instructions
The instructions below shows how to remove StoreManager Update.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the StoreManager Update.exe file for removal, restart your computer and scan it again to verify that StoreManager Update.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate StoreManager Update.exe in the scan result and tick the checkbox next to the StoreManager Update.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate StoreManager Update.exe in the scan result.



 c:\downloads\StoreManager Update.exe
c:\downloads\StoreManager Update.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If StoreManager Update.exe still remains in the scan result, proceed with the next step. If StoreManager Update.exe is gone from the scan result you're done.
- If StoreManager Update.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that StoreManager Update.exe no longer appear in the scan result.
Hashes [?]
Property Value MD5 800e348a7b4206d2d0aa5bc0e1f9a12e SHA256 354483eea7318ec5af3b85df0fd5350126cf559388c341bf0c42a31fa8bd9242
Error Messages
These are some of the error messages that can appear related to storemanager update.exe:
storemanager update.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
storemanager update.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
SetupBuilder has stopped working.
End Program - storemanager update.exe. This program is not responding.
storemanager update.exe is not a valid Win32 application.
storemanager update.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with the file?
To help other users, please let us know what you will do with the file:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.
Leave a reply